A feature Control Plane Protection permite policiamento QoS do tráfego agregado no control-plane destinado ao router processor. Desta forma e possível ter granularidade no policiamento.
Esta funcionalidade adicionada ao Control Plane Protection inclui um traffic classifier, que interceta o tráfego e classifica-o em 3 categorias no control-plane. Foram também adicionadas as features port-filtering e queue-thresholding. O port-filtering permite policiar o tráfego destinado a portas closed ou nonlistened TCP/UDP ports, enquanto queue-thresholding limita o numero de pacotes permitidos por um protocolo no control-plane IP input queue.
Beneficios do Control Plane Protection
- Extends protection against DoS attacks at infrastructure routers by providing mechanism for finer policing granularity for control-plane traffic that allows you to rate-limit each type individually.
- Provides a mechanism for early dropping of packets that are directed to closed or nonlistened IOS TCP/UDP ports.
- Provides ability to limit protocol queue usage such that no single protocol flood can overwhelm the input interface.
- Provides QoS control for packets that are destined to the control-plane of Cisco routers.
- Provides ease of configuration for control plane policies using MQC Infrastructure.
- Provides better platform reliability, security and availability.
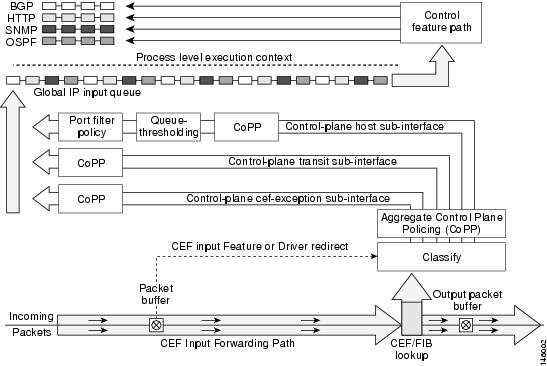
- Provides dedicated control-plane subinterface for aggregate, host, transit and cef-exception control-plane traffic processing.
- Is highly flexible: permit, deny, rate-limit.
- Provides CPU protection so it can be used for important jobs, such as routing.
Control-plane Architecture with Control Plane Protection
Control-plane Interface e Subinterfaces
O CoPP introduz o conceito de early rate-limiting protocol para tráfego especifico destinado ao processor aplicando QoS policies a interface aggregate control-plane. São disponibilizadas assim 3 control-plane subinterfaces adicionais sob o (aggregate) control-plane interface. Cada subinterface recebe e processa tráfego especifico do control-plane, estas são:
- Control-plane host subinterface: Processa o tráfego destinado a uma das interfaces do router. Exemplos:tunnel termination traffic, management traffic ou routing protocols tais como: SSH, SNMP, internal BGP (iBGP), e EIGRP. CoPP, port-filtering e per-protocol queue thresholding protection features podem ser aplicadas nesta subinterface.
Nota: Pacotes Non-IP based Layer 2 protocol como ARP ou CDP são classificados como tráfego control-plane CEF-exception subinterface
- Control-plane transit subinterface: Tráfego que atravessa o router, Nonterminating tunnels e um dos exemplos.E permitido aggregate policing para este tipo de tráfego
- Control-plane CEF-exception subinterface: Recebe todo o tráfego redirecionado como resultado de uma input feature configurada no CEF packet forwarding path para process switching ou directly enqueued no control plane input queue by the interface driver (ARP, external BGP (eBGP), OSPF, LDP, Layer2 Keepalives, e todo o tráfego non-IP host). É permitido aggregate policing para este tipo de tráfego.
Passos para configurar o CoPP:
- Ativar o QOS globalmente usando o comando mls qos, de outra forma o processamento CoPP será feito via software em vez de por hardware
- Criar ACL para classificar o tráfego. O Permit permite o matching do tráfego, o Deny causa que o tráfego será avaliado pela próxima class map.
- Criar as Class maps e associar as ACLS, IP Precedence ou DSCP values
- Criar a policy map e associar as class maps
- Sob cada class na policy map, é assignada a largura de banda permitida e especificada a acção em caso de excesso. Quando o CoPP é implementado, ambas as acções podem ser definido o transmit. Após um período de monitorização, a largura de banda pode ser afinada e a acção de excesso definida como drop (excepto para os protocolos de routing)
- Assignar a policy-map ao control plane do router/switch
Notas:
1.The type, stack, and access-control keywords were added to support FPM.
2.The type, port-filter and queue-threshold keywords were added to support Control Plane Protection.
Exemplo 1:
Efectuar drop a todo o trafego destinado a portas “closed” ou “nonlistened” excepto o NTP
class-map type port-filter pf-class
match not port udp 123
match closed-ports
policy-map type port-filter pf-policy
class pf-class
log
drop
control-plane host
service-policy type port-filter input pf-policy
R3#telnet 192.168.20.2 99
R2#
*Mar 1 01:56:43.703: %CP-6-TCP: DROP TCP/UDP Portfilter 192.168.20.1(53223) -> 192.168.20.2(99)
R2#sh policy-map type port-filter control-plane all
Control Plane Host
Service-policy port-filter input: pf-policy
Class-map: pf-class (match-all)
16 packets, 960 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: not port udp 123
Match: closed-ports
Match: not port udp 23
drop
log
Class-map: class-default (match-any)
16 packets, 966 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: any
R2#sh control-plane host open-ports
Active internet connections (servers and established)
Prot Local Address Foreign Address Service State
tcp *:23 *:0 Telnet LISTEN
udp 192.168.20.2:6500 *:0 IP SLAs Responder LISTEN
udp *:1967 *:0 RTR control LISTEN
Exemplo 2:
Configurar o queue-threshold policy e limitar as seguintes queues:SNMP(50), Telnet(50) e restantes protocolos(150)
class-map type queue-threshold match-all qt-other-class
match host-protocols
class-map type queue-threshold match-all qt-telnet-class
match protocol telnet
class-map type queue-threshold match-all qt-snmp-class
match protocol snmp
!
policy-map type queue-threshold qt-policy
class qt-snmp-class
queue-limit 50
class qt-telnet-class
queue-limit 50
class qt-other-class
queue-limit 150
control-plane host
service-policy type queue-threshold input qt-policy
R3#telnet 192.168.20.2
R2#sh policy-map type queu control-plane all
queue-limit 50
queue-count 0 packets allowed/dropped 0/0
queue-limit 50
queue-count 3 packets allowed/dropped 13/0
queue-limit 150
queue-count 0 packets allowed/dropped 0/0
Control Plane Host
Service-policy queue-threshold input: qt-policy
Class-map: qt-snmp-class (match-all)
0 packets, 0 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: protocol snmp
Class-map: qt-telnet-class (match-all)
13 packets, 786 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: protocol telnet
Class-map: qt-other-class (match-all)
0 packets, 0 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: host-protocols
Class-map: class-default (match-any)
0 packets, 0 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: any